Apache + PERMIS
The PERMIS Shibboleth Apache Authorisation Module (SAAM) is an Apache module
(version 1.3 and 2.0) that uses PERMIS to control access to websites that
use either Apache or Shibboleth to provide user authentication.
Why protect Apache web sites with PERMIS?
There are several benefits of using PERMIS with Apache. Firstly you get
the rich and fine grained authorisation infrastructure that PERMIS provides.
Secondly, when using Apache's internal authorisation system it is the administrator
of the Apache server who gives the privileges to the end-users. Embedding
PERMIS with Apache allows you to distribute the privilege management to
other people, specifically the owners of the various resources or the security
officer. Resource owners no longer need to explain to Apache administrators
who can have access to their resources - and rely on them to implement
the authorisation policy correctly. Now the resource owners or security
officers who specify the authorisation policies for the web resources can
be the very same people to create the PERMIS policies that will control
access to their the web resources.
Some technical information about Apache + PERMIS
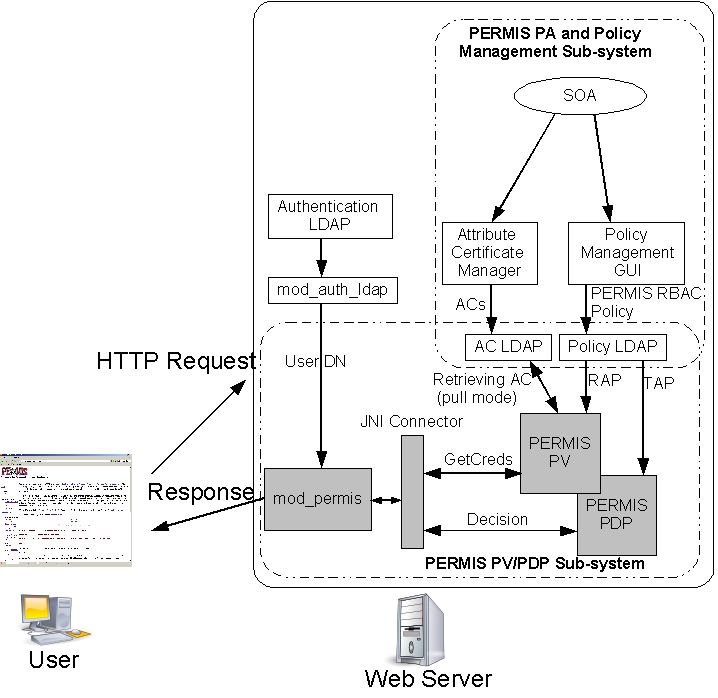
Architecure of PERMIS+Apache intergration (click on the picture
to enlarge it)
DIAGRAM LEGEND
PERMIS PV= Privilege Validator. This component checks if the attribute
assignments are valid and were carried out according to the SP's policy
PERMIS PDP = Policy Decision Point. This component makes the access
control decision based on the user's validated attributes and the SP's
policy
SOA = Source of Authority. The person responsible for the SP's policy
The interactions between SAAM, the authentication module (mod_auth_ldap)
and the Apache server are as follows:
-
When a user contacts an Apache web server, requesting access to a URL which
is protected by mod_auth_ldap and mod_permis, the user is prompted by mod_auth_ldap
to enter their username and password in order to be authenticated.
-
Mod_auth_ldap authenticates the user by searching in the authentication
LDAP server and locating the correct entry which matches the username and
password, then retrieves and puts the user's DN in the Apache HTTP header
(mod_auth_ldap has been modified so as to output the user's DN to the HTTP
header during authentication) .
-
During the authorisation phase in the HTTP request handling process, mod_permis
is invoked by the Apache server, and the user's DN is acquired by mod_permis
through the HTTP header.
-
Mod_permis calls the Privilege Validator (PV) and passes the user's DN
to it, the PV retrieves the user's ACs from the configured LDAP servers
and validates them. The PDP then makes an authorisation decision based
on the valid attributes and the configured PERMIS policy, and this is returned
back to mod_permis.
-
Mod_permis returns the decision result to the Apache server, and the user
is granted or denied access to the target resource according to the decision
result.

